Setting up Router to prevent attacks with Public Static IP SIMs
1. Background
Having a public static IP enables users to access their device from any location on the Internet, granting them extensive control over the device's functionalities as long as it remains online. However, this convenience comes with a security drawback—the device becomes visible to everyone on the Internet. Attackers exploit this vulnerability by utilizing bots to scan the entire IP address range (0.0.0.0 to 255.255.255.255). They focus on checking common ports such as 80 (HTTP), 443 (HTTPS), 23 (Telnet), 22 (SSH), and 21 (FTP). Upon receiving a response from the targeted device, attackers initiate continuous attacks, including flooding the device with millions of ping requests, attempting login with default usernames and passwords, or deploying malware to take control of the device.
For InHand cellular devices, we implement an additional layer of security by creating a console that safeguards the Linux system. This measure ensures that attackers are unable to access Linux. Nevertheless, the incessant pings or requests consume bandwidth, translating to increased costs for users in terms of data usage, ranging from megabytes to gigabytes per day. Consequently, there is a need to modify certain settings, such as altering common ports and blocking ping requests, when employing a public static IP to mitigate these security and financial risks.
This will prevent your device from responding to or accepting ping requests from the Internet, making it appear like the IP is not being or is offline. Other services like the web interface will still work.
2.1 Log into device via local connection (Default IP is 192.168.2.1) or with static IP address.
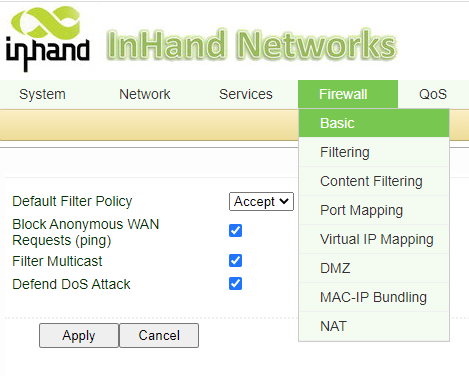
2.2 Navigate to Firewall->Basic. Check Block Anonymous WAN Requests (ping) as well as filter multicast and defend DoS Attack, these will help protect user against attacks as well as keep data usage low.
Note: Once ping is disabled, users can't ping it from internet anymore, so please make a note of this for the future when engineers need to troubleshoot.
3. Disable Ports
If common ports aren't changed, any traffic on the public static IP that goes to the ports will reach to the router, which will consume data and might slow down the bandwidth. By changing the ports to a less common number, it makes it harder for attackers to guess which port is open.
3.1 Navigate to System->Admin access.
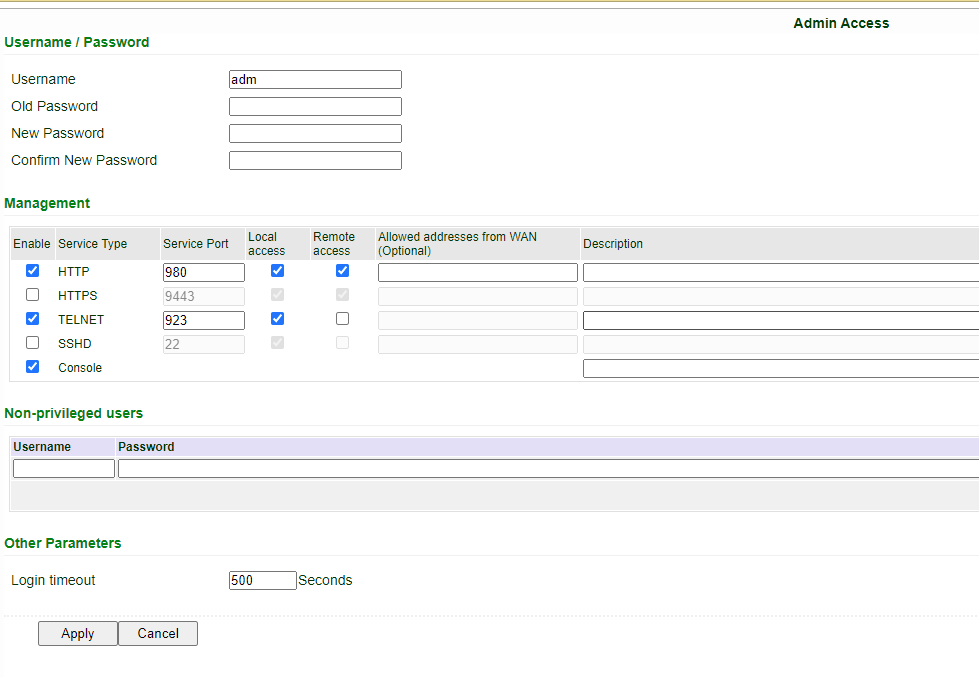
Default HTTP is 80, HTTPS 443, Telnet 23. Change the values of these Service ports or disable the port for Remote Access. Hit apply when done.
Note: Once the Remote Access is unchecked, users may not be able to access it remotely anymore. Please also make a not of any port changes, so if engineers need to access telnet or HTTP, they will know which port to access the router from.
4. Block DNS port requests
The DNS port on InHand Device is port 53, and it cannot be changed. To protect this port, we need to add Firewall filtering to block all incoming request from WAN.
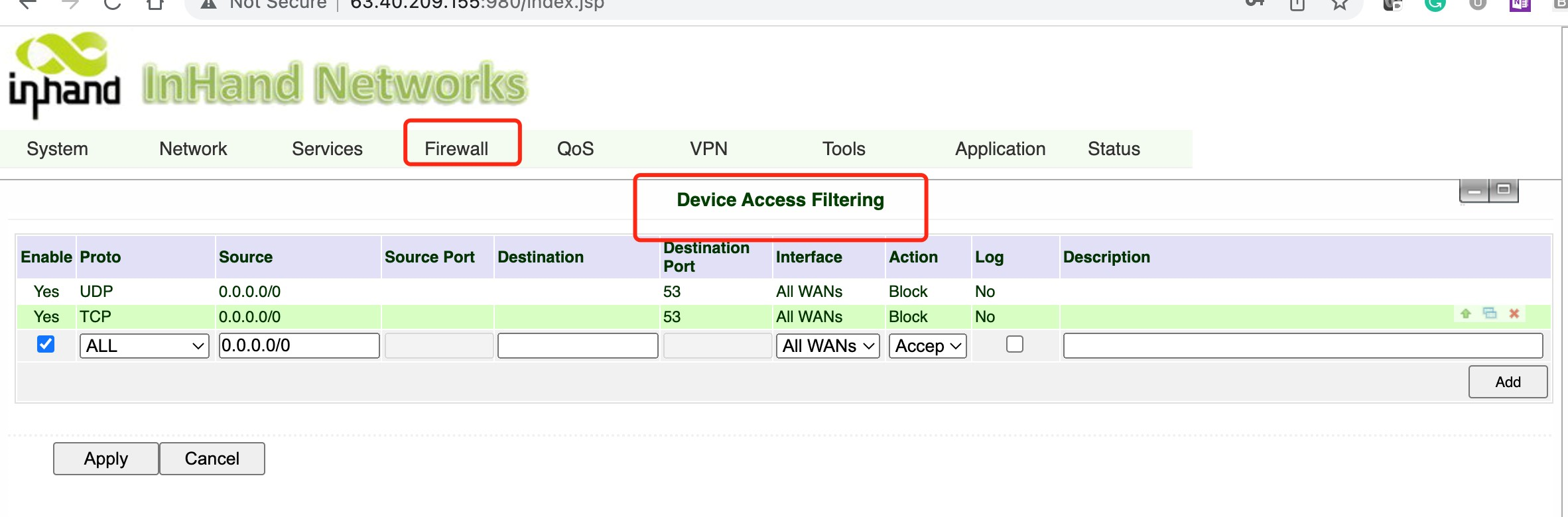
Go to Firewall>>Device Access Filtering, and add following firewall rules.
0 comments
To reply to the article, please Login or registered